In an increasingly digital world, trust is a currency that can make or break a business. Customers demand transparency, security, and reliability, and meeting their expectations goes beyond just good service. That’s where SOC 2 compliance comes into play. This comprehensive guide will unravel the complexities of SOC 2, empowering your business to establish crucial trust with clients and stakeholders alike. Whether you’re a startup or an established enterprise, understanding the principles of security, availability, processing integrity, confidentiality, and privacy in your operations is key to safeguarding your reputation. Unlocking trust through SOC 2 compliance not only boosts your credibility but also positions you as a leader in a competitive marketplace. Join us as we delve into the essential steps and best practices that will help you navigate the SOC 2 landscape, ensuring your business thrives in a trust-driven economy.
Understanding SOC
2 Compliance
In the realm of data security and privacy, SOC 2 compliance stands as a crucial benchmark for businesses operating in the digital landscape. SOC 2, or Service Organization Control 2, is a framework established by the American Institute of CPAs (AICPA) to ensure that service providers manage customer data with the utmost care and integrity. This compliance standard is not merely a set of guidelines but a comprehensive evaluation of how a company handles five key principles: security, availability, processing integrity, confidentiality, and privacy. Understanding these principles is foundational for any business aiming to build and maintain trust with their clients and stakeholders.
SOC 2 compliance is particularly important for technology and cloud computing companies that handle sensitive data. The rigorous auditing process involved in SOC 2 compliance ensures that these organizations adhere to the highest standards of data management and protection. This, in turn, reassures customers that their data is secure and processed with integrity. The emphasis on continuous monitoring and improvement means that compliance is not a one-time event but an ongoing commitment to excellence in data security and privacy.
Achieving SOC 2 compliance can also serve as a competitive advantage. In an era where data breaches and cyber threats are increasingly common, demonstrating SOC 2 compliance can differentiate a business from its competitors. It signals to potential clients that the company takes data security seriously and is dedicated to maintaining robust security practices. This can be a decisive factor for clients when choosing a service provider, thereby contributing to business growth and customer retention.
The Importance of SOC 2 Compliance for Businesses
The significance of SOC 2 compliance extends beyond mere regulatory adherence. It plays a critical role in building and maintaining customer trust, which is essential for long-term business success. In a market where consumers are increasingly aware of data privacy issues, companies that can demonstrate their commitment to protecting customer data are more likely to earn and retain the trust of their clients. SOC 2 compliance provides a tangible proof of this commitment, showcasing a company’s dedication to upholding the highest standards of data security and privacy.
Moreover, SOC 2 compliance can significantly impact a company’s operational efficiency and risk management. The process of achieving and maintaining compliance involves rigorous assessments and continuous monitoring of internal controls and processes. This not only helps in identifying and mitigating potential risks but also fosters a culture of accountability and continuous improvement within the organization. By adhering to SOC 2 standards, companies can streamline their operations, enhance their security posture, and reduce the likelihood of data breaches and other security incidents.
From a business perspective, SOC 2 compliance can also open up new market opportunities. Many organizations, particularly those in highly regulated industries such as finance and healthcare, require their service providers to be SOC 2 compliant. By meeting these standards, companies can expand their client base and enter new markets that were previously inaccessible. This can drive revenue growth and strengthen the company’s position in the industry, making SOC 2 compliance a strategic investment for any business aiming to thrive in today’s competitive landscape.
Key Principles of SOC 2: Security, Availability, Processing Integrity, Confidentiality, and Privacy
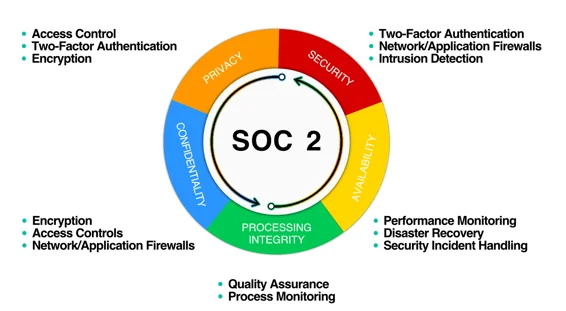
At the core of SOC 2 compliance are five key principles, each addressing a critical aspect of data management and protection. Understanding these principles is essential for any organization seeking to achieve compliance and build a robust security framework.
Security is the foundation of SOC 2 compliance. It involves implementing measures to protect data against unauthorized access, both physical and logical. This includes establishing robust access controls, encryption, and intrusion detection systems. Security also encompasses the development and enforcement of policies and procedures to ensure that data is handled securely throughout its lifecycle. By prioritizing security, organizations can safeguard sensitive information and prevent data breaches that could jeopardize customer trust and business reputation.
Availability focuses on ensuring that systems and data are accessible when needed. This principle emphasizes the importance of maintaining reliable and resilient IT infrastructure, including disaster recovery and business continuity plans. Availability also involves monitoring system performance and implementing measures to prevent and mitigate downtime. By ensuring high availability, companies can maintain operational continuity and meet the needs of their clients, thereby enhancing customer satisfaction and trust.
Processing Integrity addresses the accuracy, completeness, and timeliness of data processing. This principle ensures that data is processed correctly and in accordance with established standards and procedures. It involves implementing controls to detect and correct errors, as well as monitoring and auditing data processing activities. By maintaining processing integrity, organizations can ensure the reliability of their services and build confidence in their data handling practices.
Confidentiality involves protecting sensitive information from unauthorized disclosure. This principle applies to data that is classified as confidential, including proprietary information, trade secrets, and personal data. Confidentiality measures include encryption, access controls, and data masking. By safeguarding confidential information, organizations can prevent data leaks and protect their intellectual property, thereby maintaining client trust and compliance with regulatory requirements.
Privacy focuses on the collection, use, and retention of personal information. This principle ensures that organizations comply with privacy laws and regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). Privacy measures include obtaining consent for data collection, providing transparency about data usage, and implementing data subject rights. By prioritizing privacy, companies can build trust with their customers and avoid legal and reputational risks associated with data privacy violations.
Steps to Achieve SOC 2 Compliance
Achieving SOC 2 compliance involves a series of well-defined steps that require careful planning and execution. The process begins with understanding the scope of the audit and identifying the systems and processes that need to be assessed. This includes defining the trust service criteria that are relevant to the organization, such as security, availability, processing integrity, confidentiality, and privacy. Once the scope is defined, the next step is to conduct a gap analysis to identify areas where the current practices fall short of SOC 2 requirements.
Based on the findings of the gap analysis, organizations need to implement the necessary controls and procedures to address the identified gaps. This may involve updating existing policies, implementing new security measures, and training employees on best practices for data handling and protection. It is important to document all the changes and ensure that they are consistently applied across the organization. This documentation will serve as evidence during the audit and demonstrate the company's commitment to SOC 2 compliance.
After implementing the required controls, organizations need to undergo a readiness assessment to evaluate their preparedness for the SOC 2 audit. This assessment is typically conducted by an external auditor who reviews the implemented controls and provides feedback on any remaining areas of improvement. The readiness assessment helps organizations identify and address any last-minute issues before the formal audit. Once the organization is confident in its compliance efforts, it can proceed with the SOC 2 audit, where an independent auditor evaluates the effectiveness of the controls and issues a SOC 2 report based on their findings.
Common Challenges in the SOC 2 Compliance Process
The path to SOC 2 compliance is fraught with challenges that organizations must navigate to achieve successful certification. One of the most common challenges is the complexity of the SOC 2 framework itself. With its extensive requirements and detailed criteria, understanding and implementing SOC 2 controls can be a daunting task, especially for organizations that are new to the process. The lack of in-house expertise and resources can further complicate the compliance efforts, making it difficult to establish and maintain the necessary controls.
Another significant challenge is the continuous nature of SOC 2 compliance. Unlike other certifications that may involve a one-time assessment, SOC 2 requires ongoing monitoring and evaluation of controls to ensure their effectiveness. This means that organizations must establish a robust internal audit process to regularly review and update their controls. Ensuring continuous compliance can be resource-intensive and may require dedicated personnel and technology solutions to manage the process effectively.
Data management and integration issues also pose a challenge in achieving SOC 2 compliance. Organizations often have multiple systems and applications that handle sensitive data, making it challenging to implement consistent security measures across all platforms. Integrating these systems and ensuring that they comply with SOC 2 requirements can be complex and time-consuming. Additionally, organizations must address the human factor by providing adequate training and awareness programs to ensure that employees understand and adhere to the established controls and procedures.
The Role of Third-Party Auditors in SOC 2 Compliance
Third-party auditors play a pivotal role in the SOC 2 compliance process, providing an independent and objective assessment of an organization's controls. These auditors are typically certified public accountants (CPAs) who have specialized knowledge and expertise in SOC 2 requirements. Their primary responsibility is to evaluate the design and effectiveness of the controls implemented by the organization and determine whether they meet the SOC 2 criteria.
The involvement of third-party auditors begins with the readiness assessment, where they review the organization's controls and provide feedback on any areas that need improvement. This assessment helps organizations identify gaps and make necessary adjustments before the formal audit. During the SOC 2 audit, third-party auditors conduct a thorough evaluation of the controls, including testing their effectiveness over a specified period. They review documentation, interview personnel, and perform various tests to ensure that the controls are operating as intended.
The final output of the SOC 2 audit is the SOC 2 report, which is issued by the third-party auditors. This report provides a detailed assessment of the organization's controls and their compliance with SOC 2 criteria. It includes an opinion on the design and effectiveness of the controls, as well as any identified deficiencies and recommendations for improvement. The SOC 2 report serves as a valuable tool for organizations to demonstrate their commitment to data security and privacy to their clients and stakeholders. It also provides insights into areas where further improvements can be made to enhance the organization's security posture.
Maintaining SOC 2 Compliance: Best Practices
Achieving SOC 2 compliance is only the beginning; maintaining it requires ongoing effort and vigilance. One of the best practices for maintaining SOC 2 compliance is to establish a dedicated compliance team or committee responsible for overseeing the compliance efforts. This team should include representatives from various departments, such as IT, legal, and human resources, to ensure a comprehensive approach to compliance. The team should meet regularly to review the status of compliance efforts, address any issues, and plan for upcoming audits.
Continuous monitoring and testing of controls are essential for maintaining SOC 2 compliance. Organizations should implement automated monitoring solutions to track the performance of their controls and detect any anomalies or weaknesses. Regular internal audits should be conducted to review the effectiveness of the controls and ensure that they are operating as intended. These audits should be documented, and any identified issues should be promptly addressed to prevent non-compliance.
Employee training and awareness programs are also crucial for maintaining SOC 2 compliance. Organizations should provide regular training sessions to educate employees about the importance of data security and privacy, as well as their specific roles and responsibilities in maintaining compliance. Training should cover topics such as recognizing and responding to security incidents, following established procedures, and reporting any suspicious activities. By fostering a culture of security awareness, organizations can ensure that employees are actively contributing to the overall compliance efforts.
The Impact of SOC 2 Compliance on Customer Trust and Business Growth
SOC 2 compliance has a profound impact on customer trust and business growth, serving as a testament to an organization's commitment to data security and privacy. In a marketplace where data breaches and cyber threats are prevalent, customers are increasingly cautious about the security practices of the companies they engage with. By achieving SOC 2 compliance, organizations can provide tangible evidence of their dedication to protecting customer data, thereby enhancing customer trust and confidence.
The trust gained through SOC 2 compliance can translate into tangible business benefits. Customers are more likely to choose and remain loyal to service providers that demonstrate strong security practices. This can lead to increased customer retention and reduced churn rates, contributing to long-term business growth. Additionally, SOC 2 compliance can differentiate a company from its competitors, making it a preferred choice for clients who prioritize data security and privacy. This competitive advantage can help attract new customers and expand the company's market share.
Moreover, SOC 2 compliance can open up new business opportunities, particularly in regulated industries that require their service providers to meet stringent security standards. By achieving SOC 2 compliance, organizations can gain access to new markets and clients that were previously out of reach. This can drive revenue growth and enhance the company's reputation in the industry. Furthermore, SOC 2 compliance can streamline the sales process by reducing the need for lengthy security assessments and negotiations, as the SOC 2 report provides a comprehensive evaluation of the company's security practices.
Case Studies: Successful SOC 2 Compliance Implementation
Examining real-world examples of companies that have successfully achieved SOC 2 compliance can provide valuable insights into the process and its benefits. One such example is a leading cloud service provider that embarked on the SOC 2 compliance journey to enhance its security posture and gain a competitive edge. The company conducted a thorough gap analysis to identify areas of improvement and implemented robust security controls, including multi-factor authentication, encryption, and continuous monitoring solutions. By achieving SOC 2 compliance, the company was able to reassure its clients about the security of their data, resulting in increased customer trust and business growth.
Another case study involves a fintech startup that sought SOC 2 compliance to meet the regulatory requirements of its clients in the financial industry. The startup established a dedicated compliance team and invested in advanced security technologies to protect sensitive financial data. Throughout the compliance journey, the company focused on employee training and awareness programs to ensure that all personnel were aligned with the compliance objectives. The successful achievement of SOC 2 compliance not only enabled the startup to expand its client base but also positioned it as a trusted and reliable service provider in the competitive fintech market.
A third example is a healthcare organization that pursued SOC 2 compliance to enhance its data privacy practices and comply with industry regulations such as HIPAA. The organization implemented comprehensive data protection measures, including access controls, encryption, and regular audits, to safeguard patient information. By achieving SOC 2 compliance, the healthcare organization was able to demonstrate its commitment to data privacy and security to its patients and partners. This not only improved patient trust but also facilitated partnerships with other healthcare providers and insurers, driving business growth and collaboration.
Conclusion and Next Steps for Your Business
In conclusion, SOC 2 compliance is a critical component of building and maintaining trust in today's digital landscape. It provides a robust framework for protecting customer data and ensuring the security, availability, processing integrity, confidentiality, and privacy of information. Achieving SOC 2 compliance requires a comprehensive approach, involving careful planning, implementation of controls, and continuous monitoring. The benefits of SOC 2 compliance extend beyond regulatory adherence, enhancing customer trust, operational efficiency, and business growth.
For businesses looking to embark on the SOC 2 compliance journey, the first step is to gain a thorough understanding of the SOC 2 framework and its requirements. Conducting a gap analysis can help identify areas that need improvement and guide the implementation of necessary controls. Engaging with experienced third-party auditors can provide valuable insights and support throughout the compliance process. Establishing a dedicated compliance team and fostering a culture of security awareness are also essential for maintaining ongoing compliance.
As the digital landscape continues to evolve, the importance of data security and privacy will only increase. By achieving and maintaining SOC 2 compliance, businesses can position themselves as trusted and reliable service providers, gaining a competitive advantage and driving long-term success. Whether you are a startup or an established enterprise, investing in SOC 2 compliance is a strategic decision that can unlock trust, enhance customer relationships, and propel your business forward in a trust-driven economy.